It doesn’t matter if you’re a solo bookkeeper or running a 20-person accounting firm; you’re more vulnerable to cyberattacks than ever. According to the 2024 Verizon Data Breach Investigations Report, there was a 180% increase in breaches involving the exploitation of system vulnerabilities compared to the previous year. That means attackers are getting smarter, and firms of all sizes are at risk.
And it’s not just your data in danger. You’re also responsible for protecting your clients’ most sensitive financial information. One slip-up could lead to financial loss, legal consequences, and serious damage to your firm’s reputation.
That’s why having a Written Information Security Plan (WISP) is essential, it is an important piece of cybersecurity for accountants. A WISP outlines how your firm safeguards sensitive information, manages risk, and responds to potential threats. It’s a proactive step that helps you stay compliant, reduce liability, and build trust with your clients.
In this guide, we’ll explore:
- What a WISP is and why your firm needs one
- Key components every WISP should contain
- A simple, step-by-step process to build your own
- And a free, fully editable WISP template to help you get started quickly
What is a Written Information Security Plan (WISP)?
A WISP is a formal document that details how your firm protects sensitive data. It includes the policies, procedures, and protocols your team follows to prevent data breaches, respond to security incidents, and comply with privacy regulations.
In simple terms, a WISP is your playbook for keeping client and firm data safe from breaches.
Note: A data breach doesn’t always mean a hacker from some foreign entity is trying to break into your firm. “It could also be, ‘Oops, I inadvertently uploaded the wrong document to the wrong client’s folder.’ It really means that information was shared with an individual who was not authorized to see it,” says Brad Messner, EA.
Implementing this document is a best practice and a legal requirement in various jurisdictions and industries.
For instance, the state of Massachusetts mandates that any organization handling personal information about its residents must develop and maintain a WISP. And in the financial sector, the Federal Trade Commission (FTC) requires financial institutions (including tax preparation firms, mortgage brokers, and investment advisors) to have a WISP as part of compliance with data protection regulations. This requirement is outlined in the FTC’s Safeguards Rule, which is part of the Gramm-Leach-Bliley Act (GLBA).
Even if you’re not currently being audited or asked to show your WISP, you’re still legally required to have one under the Gramm-Leach-Bliley Act (GLBA) and the FTC’s Safeguards Rule if you run an accounting, bookkeeping, or tax firm. And beyond compliance, a WISP in place is a smart way to protect your business and your clients.
It helps:
- Strengthens your firm’s defenses against cyber threats like phishing, ransomware, and data breaches.
- Show clients and partners you take data protection seriously, which builds trust and can enhance your firm’s reputation.
- Ensures your firm can act swiftly to mitigate damage and maintain operations during a cyber event.
- Leads to more efficient workflows and reduces the likelihood of errors that could compromise data security.
Key Components of a WISP
A good WISP doesn’t have to be complicated, but it does need to cover the essentials. Here are the core components it should include and what each one means for your firm:
Information Security Policy
This is the foundation of your WISP. It outlines your firm’s commitment to protecting sensitive information and sets the tone for handling security across your business. It should include:
- What types of data you collect and manage
- Why protecting that data matters
- Who’s responsible for overseeing security in your firm
Risk Assessment
This section identifies the specific threats and vulnerabilities that could affect your firm. Think of it as taking stock of what could go wrong and planning how to prevent it.
Your risk assessment should cover:
- Where sensitive data is stored and accessed (local drives, cloud apps, etc.)
- Who has access to that data
- Common threats like phishing, ransomware, or lost devices
- The likelihood and potential impact of each risk
It’s important to revisit this at least once a year, especially if your systems or processes change.
Access Control Measures
Not everyone in your firm should have access to everything. Access control helps you protect data by making sure only the right people can see or handle certain information.
This section should outline:
- Role-based access: who can access what
- Password management rules (length, complexity, update frequency)
- Multi-factor authentication (MFA) use
- Procedures for revoking access when someone leaves the firm
Limiting access helps reduce the chance of internal mistakes or unauthorized exposure.
Data Encryption & Secure Storage
Encryption protects sensitive data while it’s stored and when it’s being shared.
Your WISP should include:
- How and where data is encrypted (e.g., emails, backups, cloud storage)
- Whether full-disk encryption is enabled on company devices
- Secure file-sharing practices for working with clients and team members
- Storage tools used (e.g., Dropbox, Google Drive, or practice management software like Financial Cents)
This shows you’re actively preventing unauthorized parties from reading your firm or client information.
Incident Response Plan
No matter how good your security is, things can still go wrong. An incident response plan tells you exactly what to do if that happens. It helps you act quickly and minimize the damage.
This section should spell out:
- What counts as a security incident
- The steps to take if there’s a data breach (identify, contain, notify)
- Who’s responsible for each action
- How to document the event and report it to the right people (internally and externally)
Employee Training & Awareness
Your team can be your strongest defense or your biggest risk. That’s why regular training is key.
This part of your WISP should include:
- New-hire onboarding: what security topics they’re trained on
- Ongoing education: phishing simulations, refresher courses, etc.
- Policies employees must follow (e.g., no personal devices for client work)
- What to do if they notice something suspicious
Free WISP Template Download [Word]
Written Information Security Plan (WISP) Template
How to Create a WISP for Your Accounting Firm
Creating a WISP might sound overwhelming, but it doesn’t have to be. Follow these steps to build an effective one for your firm, whether you’re a solo accountant or managing a team.
1. Assess Your Firm’s Current Data Security Measures
Start by evaluating the data security protocols you currently have in place. Look at how your firm handles sensitive data—do you limit access and implement strong passwords?
Review tools like accounting software, file-sharing platforms, email systems, and cloud storage to ensure they have safety measures. If you’re using free or low-cost solutions, they’ll probably not have the proper security, says Brad.
Also, check the physical security of your offices (if you have one) to prevent unauthorized physical access to sensitive information.
Knowing your current data security measures will give you a baseline to work from.
2. Identify Risks and Vulnerabilities
Next, list out the potential ways data could be compromised in your firm. Think about both internal and external risks like employee errors, weak passwords, phishing attempts, outdated software, or unsecured Wi-Fi in remote work settings.
3. Define Roles and Responsibilities Within Your Firm
Security isn’t just an “IT” thing, it’s a firm-wide responsibility. In your WISP, clearly define who’s in charge of what. For example:
- Who handles employee training?
- Who monitors software updates and access logs?
- Who reports and responds to suspicious activity?
If you’re the only person in the firm, that’s fine; just note your responsibilities clearly.
3. Develop Security Policies for Data Protection and Access Control
This is the core of your WISP. Document how your firm protects client and internal data. Make these policies practical and easy to follow. Some policies to include:
- Strong password requirements and how often they should be updated
- Two-factor authentication (2FA) for software and devices
- Rules for sharing files securely (like no sensitive data in plain-text emails)
- Remote work protocols
- Data access based on job roles
- Procedures for collecting, storing, and disposing of sensitive information
4. Establish Protocols for Responding to Security Incidents
No one likes to think about worst-case scenarios, but you need a plan. Your WISP should include clear steps to take in case of a data breach or security incident.
Outline:
- How to identify a security breach
- How incidents should be reported
- Who needs to be notified (internally and externally)
- What steps to take to contain the issue
- How to document and review what happened
5. Regularly Review and Update the WISP
Your WISP isn’t a “set it and forget it” kind of document. Cyber threats evolve, and so should your plan. “You have to regularly review our policies. You have to go through with updates and make sure that you’re performing proper maintenance on your systems,” Brad says.
So, set a reminder to review your WISP every 6–12 months or whenever there’s a major change in your software, processes, or team structure. If you onboard a new team member or switch to a new tool, update the plan accordingly.
You may be interested:
Best Practices for WISP Implementation
Creating your WISP is a great first step, but putting it into action is what really matters. Here are a few best practices to help you implement your plan effectively and keep your firm protected in the long term.
Regular Employee Training on Data Security
Even the best-written security policies won’t work if no one follows them. Make sure everyone in your firm understands the WISP and knows what’s expected of them, especially when it comes to handling client data.
Schedule regular training sessions to cover how to recognize phishing emails and scams, secure password practices, report suspicious activity, and act in the event of a data breach.
If you’re a solo firm, this is still important. Block time every few months to review your own security habits.
Update Policies Based on Evolving Cybersecurity Threats
Cybersecurity threats are always changing. What worked a year ago might not be enough today. Make it a habit to revisit and update your WISP regularly, especially when you adopt new tools or software, your team grows or roles change, you hear about a new threat affecting similar businesses, etc.
Use an Accounting Practice Management Tool
The tools you use play a big role in keeping data safe. Generic file-sharing apps or outdated platforms often leave gaps in your security.
Instead, use tools that are built with accountants and bookkeepers in mind, like Financial Cents. As Brad says,
One of the reasons why I do really love Financial Cents, is it makes it so easy you don't even recognize that they're applying security behind the scenes at every step."
And he’s right. Financial Cents helps you manage your workflow and securely share files with your team and clients. It uses OpenSSL to provide AES-256 and AES-128 encryption, and all encrypted values are signed using a message authentication code (MAC), so they can’t be modified once encrypted.
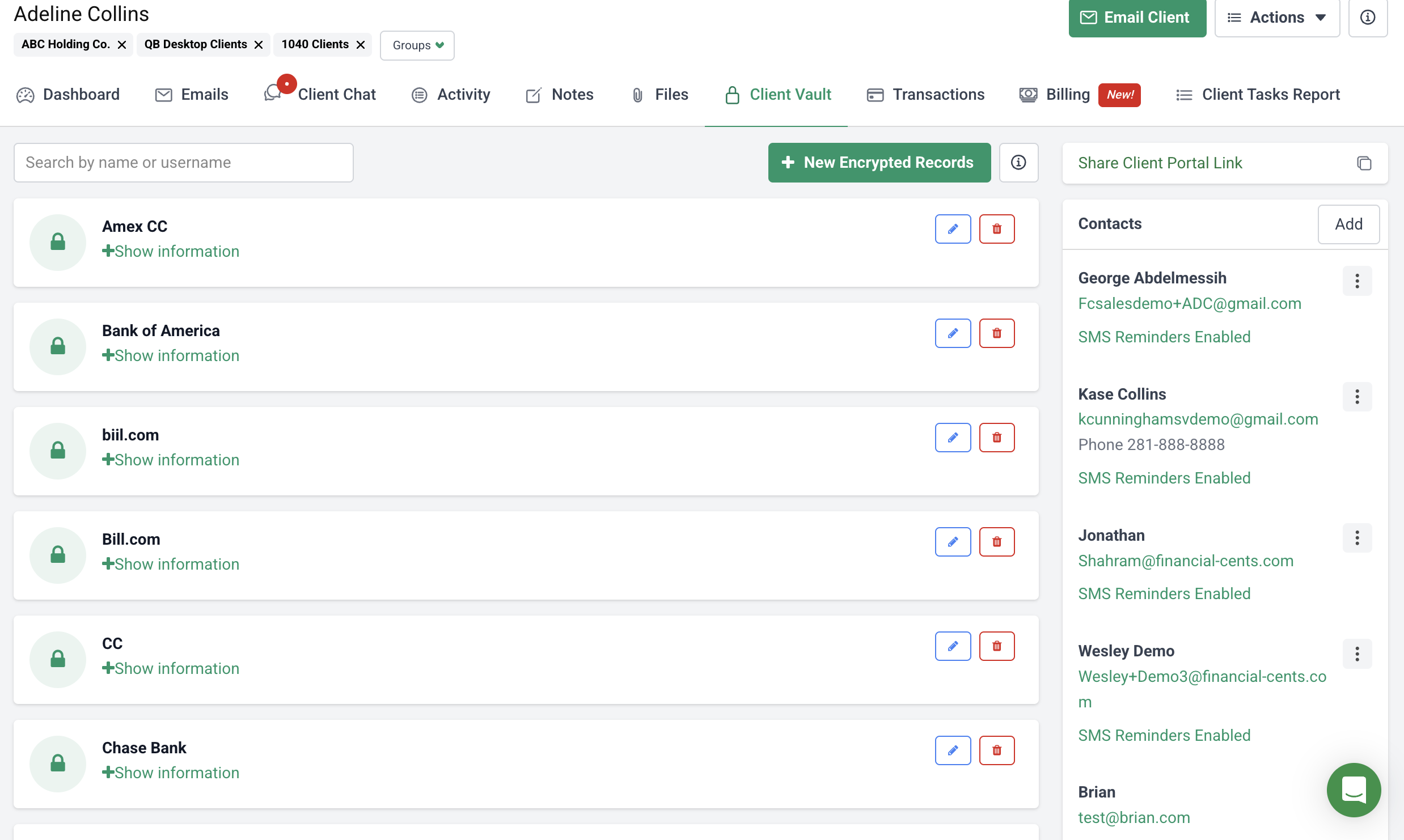
Financial Cents also includes Client Vault, which is a secure way to store and share client passwords and other sensitive information. This ensures your team has access to the data they need, without compromising security.
You can find the Client Vault in your Client CRM, under each client’s profile page:
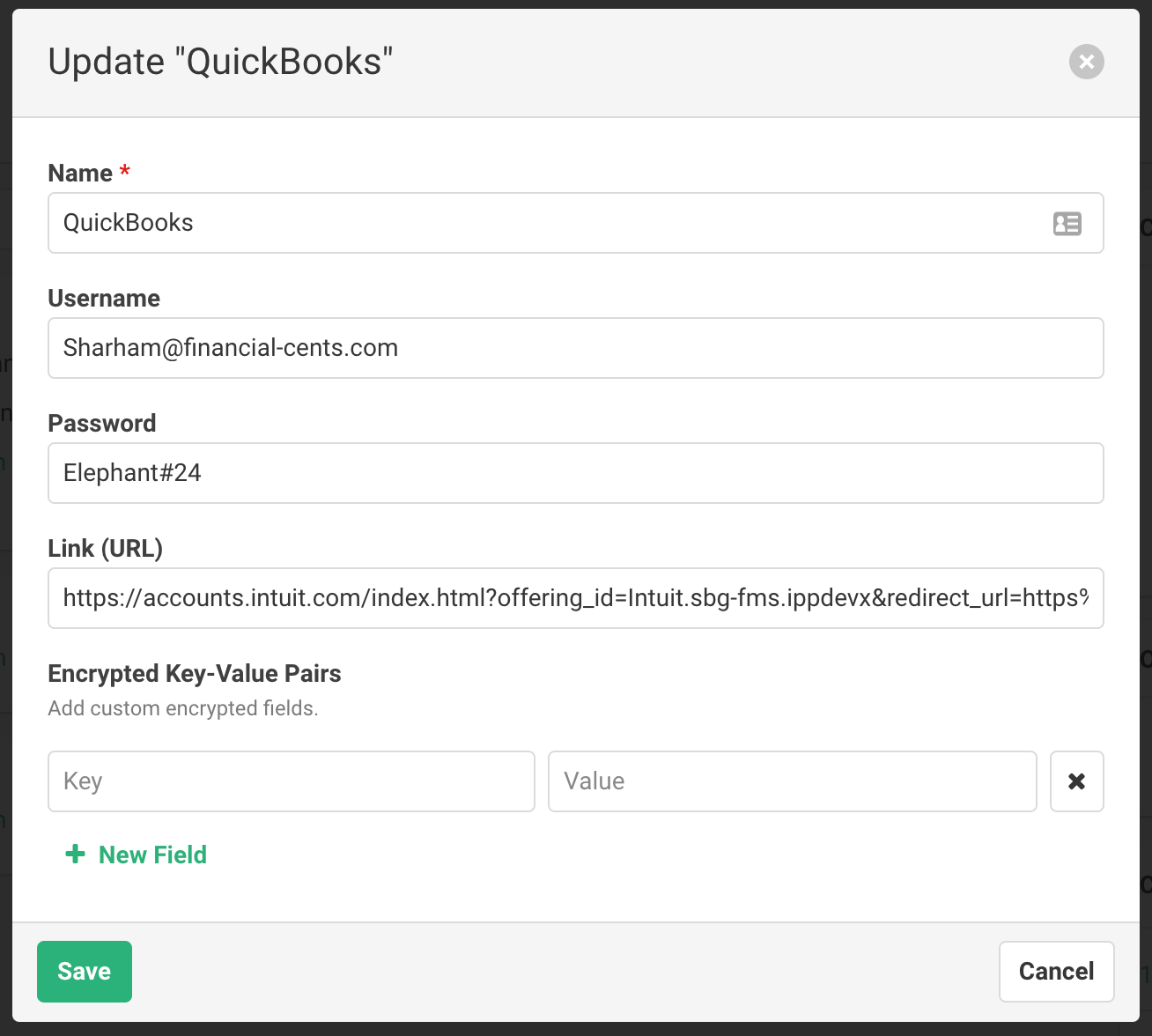
To add a new encrypted record, click “+ New Encrypted Record” and input the necessary information.
- Name – Name of the app, bank, or credit card
- Username – Username for login
- Password – Password for login
- Link – Link to the app’s login page
- Encrypted Key-Value Pairs – Custom fields that store other information like security questions, etc.
Final Thoughts
A WISP protects your clients, your firm, and your reputation. With cyber threats on the rise, having a clear, easy-to-follow plan helps you stay secure, build trust, and respond confidently if something goes wrong.
Using a WISP template gives you a structure to follow, saves time, and helps you cover all the critical areas without missing a step.
And remember, your tool of choice matters. A secure, accounting-specific platform like Financial Cents can make WISP implementation seamless. From secure file sharing to client communication, it helps you protect your sensitive information and comply with regulations.
Use Financial Cents to Manage Your Accounting Practice.